Description
Description
The SQL Server architecture has been turned out through the experience a long back ago. And the application level alterations can be the most effective that has to be performed for altering the changes in the application level. And the process doesn't have much control over the third party applications and won't disturb the application that have been specified in the SQL Server database and that doesn't have much control over the internal applications.
The architecture of SQL Server consists of the following types such as:
- Data file architecture
- Memory architecture
- Log file architecture
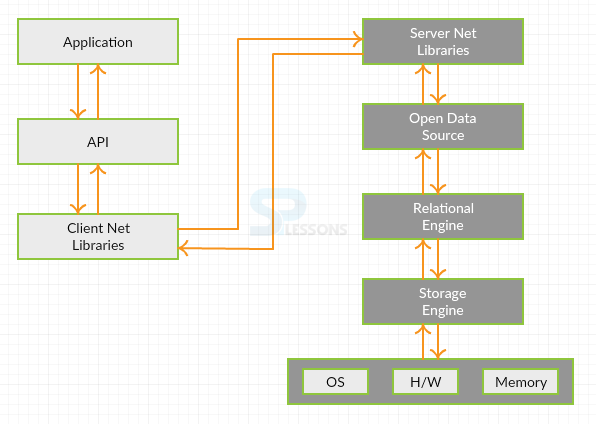
 Conceptual
figure
Conceptual
figure
- Application - Is program designed to perform a specific task.
- API - Application programming interface.
- Client Net -Is a back offive resource for SQL Server.
- Server Net Libraries - Is an SQL Server instance in the lost host.
- Open Data Source - Is an open source application.
- Relational Engine - Is a query processor.
- Storage Engine - Is a database engine.
- OS - Is an operating system.
- H/W - Is the physical aspects of a computer.
- Memory - Is physical device for storing information.
 Description
Description
The data file architecture consisting of user defined functions that are specifically assigned file groups such as:
In SQL Server there are three types of files such as primary data file,secondary data files and log files.The primary data file has an extension with .mdf and the secondary data files has an extension with .ndf and the third is the log file and has an extension with .ldf.
For extents major part of the disk space is specified for indexes and tables.These extents consisting of 64KB with contiguous pages.And these extents are of two types such as mixed and uniform.The mixed extents are created with 8 objects and uniform extents are created with a single objects.
Pages are the significant parts in the information storage of SQL Server.And these pages are utilized to store the page type and the measure of accessible plate space and the items that are keeping up inside the page.
File groups can be classified into client characterized and essential files. client characterized file groups are the file groups that are determined by utilizing the file group keyword in the database statements. And essential files group contains only the primary informational records.
- Files
- Extents
- Pages
- File groups
 Description
Description
One of the essential plan objectives of all database programming is to minimize circle I/O since disk peruses and composes are among the most asset serious operations. Memory in windows can be called with Virtual Address Space, shared by User mode and Kernel mode.
Buffer administration is a key segment in accomplishing I/O very effectiveness. The buffer administration segment comprises of two instruments: the buffer manager to access and redesign database pages and the buffer pool to decrease the database records I/O. The buffer pool is further isolated into numerous segments. The most important ones being the buffer cache and procedure cache. Buffer cache holds the informational pages in memory so that as often as possible got to information can be recovered from reserve.
Holds SQL Server occasion level information about databases and locks.
Saved for perusing and composing exchange log pages.
Windows allots stack space for every string began by SQL Server.
 Description
Description
The SQL Server transaction log operates logically as if the transaction log is a string of log records. Each and every log record is distinguished by Log Sequence Number (LSN). All the log record contains the ID of the transaction has been placed.
Log records for information adjustments record either the sensible operation executed or they recorded it previously, then after the fact pictures of the changed information. The before picture is a duplicate of the information before the operation is played out, the after picture is a duplicate of the information after the operation has been performed.
There are to methods for recovering an operations that depends on log records.
For rolling the logical operation forwarded the operation is performed. And for performing the logical operation back the reverse logical operation is performed.
To roll the operation forward the after image is applied and to roll the operation back the before image is applied.
- Logical operation logged
- Before and after image logged
 Key Points
Key Points
- Architecture - Most effective for performing the changes in the application level and have control over internal applications.