Description
Description
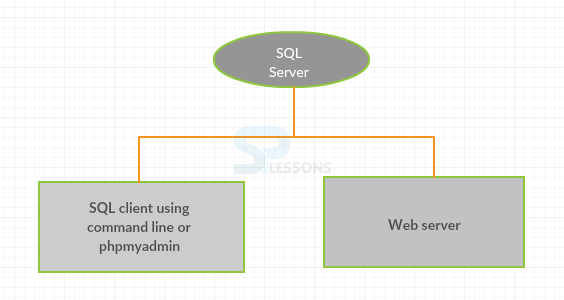
Control Access Lists are used in SQL for each and every query operations and connections, that are a part of security for accessing the database accounts. There is additionally bolster for SSL-encoded associations among SQL servers and SQL users. A significant number of the ideas performed are not particular to only SQL database and the same general thoughts apply to all the functions.
A resistance inside and out system, with covering layers of security, is the most ideal approach to counter security dangers. SQL Server gives a security engineering that is intended to permit database overseers and designers to make secure database applications and counter dangers.
 Description
Description
The following steps explain some of the key instructions related to Security related to database.
Applications performed in SQL ought not believe any information listed through clients, and ought to be composed utilizing legitimate cautious programming strategies.From the web, the information ought not be transmitted in plain content. This data is open to everybody who has room schedule-wise and capacity to block it and use it for their own particular purposes. Rather, utilize an encoded convention. For example, SSH or SSL. SQL bolsters interior SSL associations. Another strategy is to utilize SSH port-sending to make a scrambled channels for the correspondence.
- While performing the installation of database every records ought to be keep up legitimately and ought not unveil to anybody.
- To get to the database tables the root account assumes a key parts.
- SQL uses revoke and grant privileges for accessing all the necessary controls that are related to the database.
- SQL database passwords ought to be in clear content and contains the qualities that are a part of hash.
- Execute strings and tcpdumps functions and check the information in the database are decoded are not.
 Points
Points
- Security - Are the privilege measures that are taken as a part of the database.