Description
Description
OBIEE 11g is a Business Intelligence (BI) instrument by Oracle Corporation. Its demonstrated design and regular framework for creating and conveying dashboards, venture reports, scorecards, specially appointed examination, and OLAP investigation gives a rich end-client encounter. This instructional exercise clarifies all the essential parts of OBIEE. An arrangement of BI apparatuses will be given by Oracle Corporation. It empowers the client to convey vigorous OLAP, dashboard, arrangement of reporting, impromptu inquiry and investigation and scorecard usefulness with a rich end-client encounter that incorporates, cautions and numerous representation.
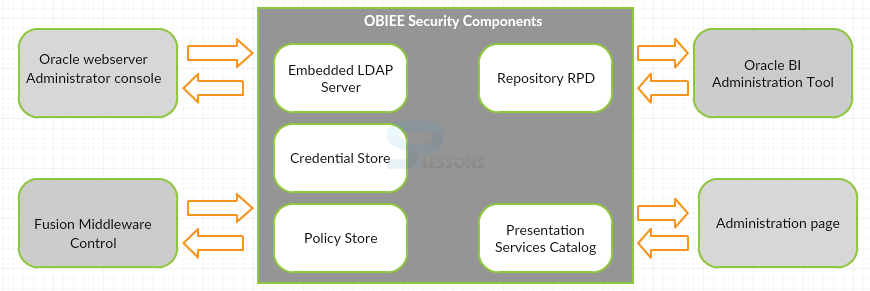
OBIEE security is characterized by the utilization of some control models for accessing the role based method. It is characterized in certain adjustments to various registry server gatherings and clients. By defining all the segments that are characterized to create a security strategy. All the Security structure can characterize with these accompanying parts.
- The index Server User and Group oversees by the Authentication issuers.
- The application parts oversees by the Policy store that gives Security approach the accompanying segments such as Presentation inventory, vault and arrangement store.
 Description
Description
Security strategy in OBIEE is partitioned into the accompanying parts such as:
- Presentation Catalog
- Policy Store
- Repository
 Description
Description
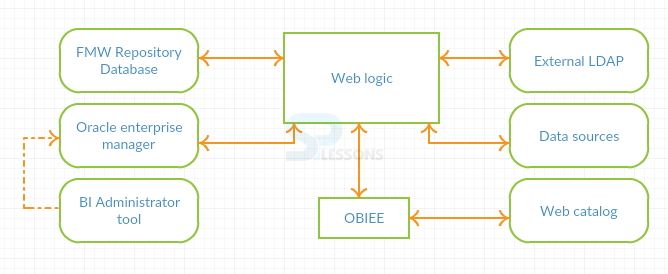
Security supplier will be called in mind and the end goal to get the security data. Accompanying sorts are the sorts of security suppliers that are utilized by OBIEE.
- Authentication provider to validate clients.
- Credential store provider is utilized to store accreditation utilized inside by the BI application.
- Policy store provider is utilized to give benefits on all applications aside from BI Presentation Services.
 Key points
Key points
- Security - Is used for characterizing some specific models.
- Security policies - Describes the security strategy in OBIEE.
- Security providers - Also called as mind and the end goal to the security.